[quote]
Cryptography by Merriam-Webster
1: secret writing
2: the enciphering and deciphering of messages in secret code or cipher; also: the computerized encoding and decoding of information
[/quote]
Did you know that 4000 years ago humans were encrypting messages? You might be wondering how since it was only in the last century that we invented computers. What many don’t know is that cryptography is simply hiding a message within a code. Encrypting it so that only those with a need to know can read the message. Even if it’s intercepted it can’t be read. This cryptology can be done on a piece of paper, in tree bark, in a treasure chest…you name it.
While it was originally invented as a form of art back in ancient Egypt around 2000 B.C. to decorate tombs and tell a story, it quickly became an integral piece of warfare. Secrets needed to be kept secrets. Since the explosion of the internet and world wide web cryptology has also taken off. This tends to lead to the assumption that encryption is some recent development. Like it only exists in The Matrix.
Another false assumption is that cryptology provides encryption algorithms that will never be broken. Every algorithm will be broken one day. All it takes is enough resources and time to make that happen. Considering this, the goal of cryptology is to make it too expensive, time consuming and work intensive for the hacker or interested party that it’s not worth their time and money. At this point in time there are algorithms that would take millions of years to break. But as technology advances getting smaller and faster, so does that window of time it takes to break the code.
Note: Another term for encryption is cipher
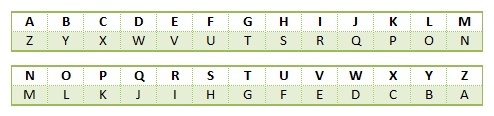
At-bash: Ancient Hebrew Cryptography (A Substitution Cipher)
Did you figure out how it works? My name, John, encrypted is “QLSM”. What about yours?
Scytale Cipher: Ancient Spartan Encryption Method
Around 400 B.C. they invented a unique type of cryptography. It involved a sheet of papyrus (type of paper) and wooden rod or stick. They would write a message on the papyrus while it was wrapped around the stick. The papyrus would then be delivered and could only be read by the recipient if he had the right stick. Otherwise the words wouldn’t line up.
Caesar Cipher: 3 places to the left (A Monoalphabetic cipher)
Can you see what Julius Caesar did? My name, John, encrypted is “NSLR”. What’s yours? This might seem way to simplistic. But remember that back then hardly anyone knew how to read so this was pretty intense stuff. “It’s only 4 letters so we can break it. Then learn how to read!”
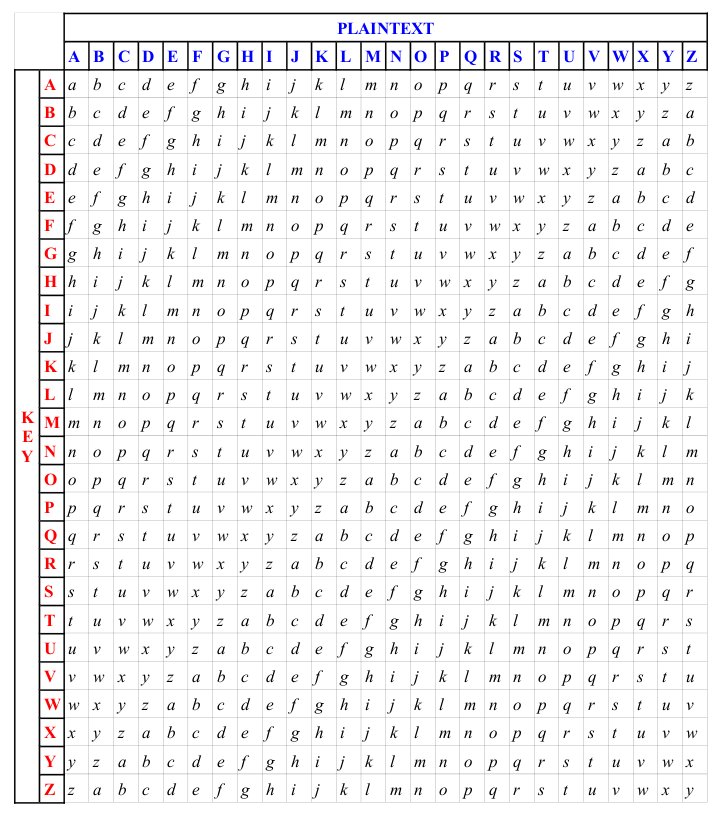
Vigenere Table (A Polyalphabetic substitution cipher)
This one is a bit more complicated and was invented in the 16th century for Henry III. It was modeled after the Caesar Cipher but instead of 3 places to the left and only 2 rows it has 27 rows and each row moves 1 place to the left. Check out the image to the right…it will really help grasp it better.
Key (Password): John
Plaintext message: Use the force
Ciphertext message: DGL GQS MBAQL
Not sure how that worked?
Use The Force
Joh nJo hnJoh
Did that help? “U” is the Text Reference and “J” is the Password Reference. The reason there are 27 rows is so that the same coded letter doesn’t get assigned twice. For example, the letter “E” in all 3 words. Notice how in the first and last word it is coded to L but in the second word it’s an S? It’s preferable this doesn’t happen cause it could assist the hacker in decoding. You can see one reason why we don’t use this one anymore. But compared to the Caesar Cipher and in the 16th century it was advanced.
For a more in-depth explanation click here.
Germany’s Enigma Machine: World War II Era (Most Famous Cipher Machine)
The Enigma Machine is probably one of the most famous because of the affect it had on World War II. It was developed by Germany after World War I around 1923 and had many models/upgrades after and was crucial to Germany’s military during WWII. Breaking it’s code and Germany not knowing helped turn the tides in the Allies favor. I’ve heard it sped up the war by 2 or 3 years and saved countless lives.
How did it work?
The basic operations were pretty simple. The Enigma machine on both ends, sender and receiver, would set their electric and mechanical settings to a predecided combination. If both did not use the same setting then it wouldn’t work. As the sender typed a message in, the Enigma Machine would replace that letter with a different one. So the plaintext would come out garbled (ciphertext). The sender would then morse code it over the radio. The receiver would get it and retype the ciphertext and the Enigma Machine would spit out plaintext.
Note: Plaintext is the readable message and Ciphertext is when it’s encrypted.
William Frederick Friedman wrote a book called The Index of Coincidence and Its Applications in Cryptography in 1920 and he’s known as “The father of modern cryptography”. He also broke a lot of code for the US Army in WWII.
Last Couple Decades:
Now we have way more advanced algorithms in cryptography like Asymmetric, Symmetric, Block Ciphers, Stream Ciphers, Public Key Cryptography, PGP (Pretty Good Privacy), Steganography (Hiding data in other media) and more. All help provide AIC (Availability, Integrity and Confidentiality). You might be more familiar with these in other terminology like WPA2/AES on your router for WIFI and it is a secure symmetric algortihm. WEP is also symmetric but easily broken. Never use it. Also don’t use WPA/TKIP. It’s too weak. You might have heard of PKI (Public Key Infrastructure) which is an asymmetric algorithm and commonly used with encrypting and digitally signing email. This can get way deeper than you need to know. 
Many algorthims become public knowledge and it is the key that is kept secret. For example, all the above algorithms I mentioned there is no secret to how they work. But the keys generated by them should always be kept secret. Auguste Kerckhoff publish a paper in 1883 saying the only thing you need to keep secret in Cryptography is the key. On the other hand, many algorithms are kept secret so no one knows how they work. Most governments prefer this method because they don’t want anyone knowing how they encrypt their messages.
The fascinating part is how long we (humans) have had Cryptography and the role it’s played in war and peace. You’ve probably seen or read The Davinci Code and found the code fascinating and intriguing to figure out as you went along with the story. How about the cryptex in that story? We use Cryptography everyday to protect life-threatening secrets. In the new James Bond movie Skyfall (Spoiler Alert) a hard drive is stolen with the identities of all hidden agents. Even though it was encrypted they were able to break it to reveal the identities.
So why do we have Cryptography? Maybe to keep me employed…since I’ve been working in IT for little over a decade and in Information Assurance for about half of that. But this is not the real reason we have cryptography. It’s to provide algorithms to encrypt messages. To keep secrets as secrets. Is there an unbreakable algorithm? Nope. All algorithm’s will be broken one day. The goal of cryptography is make it too tough to break the code that it’s not worth the hackers time. Today’s best encryption could be replaced tomorrow.




Good post. I had heard that people were doing things like this thousands of years ago. It always amazes me that we think that people 4,000 years ago were not advanced, and things like this blow up that theory in my opinion.
Thanks John! I agree…kind of like the pyramids and other great wonders of the world. Engineers have been around a long time. On a side note, I thought it was interesting how they called humans “creator” Engineers in the movie Prometheus.
Qlsm,
I remember reading about the Enigma Machine somewhere along the line. Thanks for the explanation about how it worked.
As I recall, one code that Germany could never break was the Navajo Code Talkers, because they used their ancient language to send messages. Have you seen the movie about the Code Talkers?
Gviib
I remember hearing about the Navajo Code Talkers and have seen the movie. That is an interesting fact that on top of breaking the code you have to speak the language. Maybe I should include them in here…
Awesome job coding your name!!!
I always loved the word steganography. It made the process sound so much more fun and exciting than it actually is when you get down to the 1’s and 0’s. =)
When talking about cryptography and its weaknesses, I think it’s always helpful to also remember that social engineering is far more common than cryptographic attacks – and it is the one aspect in protecting our information over which we have much control.
The social engineering challenge at defcon is a good reference for people who are unfamiliar with the concept – http://money.cnn.com/2012/08/07/technology/walmart-hack-defcon/index.htm. But the basics – beware of sharing information – intentionally or otherwise.
Thanks for commenting and sharing the link. You’re absolutely right that social engineering is very common. And most data integrity loss comes from human error (not intentional) by simply not knowing and even sometimes having good intentions.
the lock code means calling card